Update: Surfshark and Atlas VPN sent us statements explaining the rationale behind the inclusion of their own CA certs and what is being done to remediate the current situation, click here to read .
Several well-known VPN providers - including Surfshark , TurboVPN and VyprVPN - are among six brands called out for a risky practice that potentially undermines user security.
As part of its Deceptor programme , security research firm AppEsteem found that providers’ apps install a trusted root certificate authority (CA) cert on users’ devices and some providers even fail to obtain users’ consent for doing so.
AppEsteem recently expanded its programme to include VPN providers, researching VPN apps to look for deceptive and risky behavior that could harm consumers.
Not good practice
AppEsteem also pointed out that popular VPN provider Surfshark installs its root CA cert on the user’s device even when the user cancels the installation. Surfshark clearly mentions the use of its own trusted root certificate “solely to connect to VPN servers using the IKEv2 protocol”.
TechRadar Pro ’s security expert, Mike Williams, stated “Installing trusted root certificates isn’t good practice. ‘If it’s compromised, it could allow an attacker to forge more certificates, impersonate other domains and intercept your communications.”
What are the risks of installing an additional trusted root certificate?
Root CA certs are the cornerstone of authentication and security in software and on the Internet. They’re issued by a certified authority (CA) and, essentially, verify that the software/website owner is who they say they are.
The installation of an additional root CA cert potentially undermines the security of all your software and communications. When you include a new trusted root certificate on your device, you enable the third-party to gather almost any piece of data transmitted to or from your device.
Plus, an attacker who gets hold of the private key that belongs to a trusted root certificate authority can generate certificates for his own purposes and sign them with the private key.
This applies to software applications, websites or even email. Anything from a man-in-the-middle attack to installing malware is possible, as illustrated by hacks in 2021 in Mongolia and in 2020 in Vietnam where CAs were compromised.
The power that Root CA certs have over a user’s device is why state actors like Russia have been pushing citizens to install their new root CA , a move that EFF describes as “paving the way for a decade of digital surveillance”.
The six VPN providers that were found to install root CA certs on user devices are Surfshark, Atlas VPN, VyprVPN, VPN Proxy Master , Sumrando VPN and Turbo VPN . Two of the better known providers on the list, Surfshark and Atlas VPN, both recently joined NordVPN’s parent company Nord Security. However, NordVPN was not among the named providers.
Why would a VPN company want to install a trusted root certificate?
We don’t believe that’s necessary even for IKEv2 compatibility, and most top-rated VPNs do not do this.
When an additional root CA cert is installed by a VPN provider, you are relying only on the provider’s encryption and authenticity checks, as the trusted root certificate can overwrite the encryption and authenticity checks of the actual service you’re using (e.g. Mozilla Firefox , WhatsApp).
This makes it possible for the VPN provider to intercept and monitor essentially all your traffic, in a worst case scenario. We’ve reached out to Surfshark, Atlas VPN and VyprVPN and will update the article when we hear back.
The official statement we received from Surfshark and AtlasVPN
Surfshark
When using the Surfshark root certificate, customers put their trust only in a VPN provider and not a third-party agency that can be compromised. Over the past years, we’ve seen numerous cases where third-party CAs were discredited. Surfshark is a trusted cybersecurity company and ensuring the security of our products and the privacy of our customers is our core goal. Building that trust is paramount to us. As for AppEsteem’s evaluation, we’ve closely cooperated with the company in quickly fixing the highlighted issues. All of them have already been fixed and all Windows users should soon receive an updated version of the app. Also, we’ve been working on turning off the no longer popular IKEv2 protocol and focusing all our efforts on supporting Wireguard and OpenVPN protocols. This will eliminate the need to install the certificate.
AtlasVPN
At Atlas VPN, our priority is to ensure security and privacy across all aspects of our services. Differently from most of the VPN providers, we decided to build our Windows client around the IKEv2/IPSec protocol instead of an older OpenVPN protocol. We chose IKEv2/IPSec as a more modern, more efficient, and faster alternative, which is also natively supported by many OSes. In order for the IKEv2-based client to work properly and to be secure, we had to issue our own certificate instead of relying on a third party. MiTM attack would only be possible if private keys of our root certificate are compromised, this applies to every issuer of certificates around the world, and we trust in our ability to safeguard it. In the end, having Atlas VPN will significantly reduce the risk of MiTM attack compared to browsing without a VPN at all. We’re actively cooperating with independent reviewers, including AppEsteem, and we’ve always considered such cooperation crucial for improving our service. When it comes to AppEsteem’s analysis, we’re working on adjustments to provide more transparency and information regarding the functioning of our application, and the updated Windows app will be released soon.
Earth may have narrowly avoided a devastating comet impact 1,600 years ago
Earth may have had a near-miss encounter with a comet nearly 2,000 years ago that would have devastated the planet, if its debris is anything to go by.
Between 252 and 383 CE, 69 near-Earth comets were recorded by Chinese astronomers, and researchers at the University of Cincinnati found evidence that one of these comets came close enough to Earth that debris from the comet exploded in the atmosphere over the Ohio River Valley region of North America.
Such explosions, known as airbursts, are incredibly destructive and can generate orders of magnitude more energy than even our most powerful nuclear weapons. And when such an airburst occurs over a populated region, the results on the ground are nothing short of apocalyptic.
According to the new study, published in the Scientific Reports journal, artifacts and other evidence uncovered at 11 sites belonging to the indigenous Ohio Hopewell culture spread out across the region indicate that up to 9,200 square miles were set ablaze by the explosion.
This is an area more than 10 times the size of the Tunguska event in 1908 when a similar airburst leveled 830 square miles of forest in Siberia, Russia.
Several Algonquin and Iroquoian tribes, which are descended from the older Ohio Hopewell culture, have consistent oral histories that harken back to a terrible calamity at some point in the past, said Kenneth Tankersley , the study's lead author and a professor of anthropology at the University of Cincinnati's College of Arts and Sciences.

"What's fascinating is that many different tribes have similar stories of the event," Tankersley said.
"The Miami tell of a horned serpent that flew across the sky and dropped rocks onto the land before plummeting into the river. When you see a comet going through the air, it would look like a large snake.
"The Shawnee refer to a 'sky panther' that had the power to tear down forest. The Ottawa talk of a day when the sun fell from the sky. And when a comet hits the thermosphere, it would have exploded like a nuclear bomb."
Tankersley and his co-authors believe that the airburst not only laid waste to the corn crop that the Hopewell people relied on, it also destroyed just about any other source of food in the region.
"It looks like this event was very injurious to agriculture. People didn't have good ways to store corn for a long period of time. Losing a crop or two would have caused widespread suffering," said David Lentz, a professor of biology at the University of Cincinnati and co-author of the study.
"When your corn crop fails, you can usually rely on a tree crop. But if they're all destroyed, it would have been incredibly disruptive," Lentz added.
The study suggests that the airburst might have been the inciting cause for the Hopewell culture's sudden and rapid decline around this period.
"It's hard to know exactly what happened. We only have a few points of light in the darkness," Lentz said. "But we have this area of high heat that would have been catastrophic for people in that area and beyond."
Analysis: Now just imagine if it actually hit us
There's no way to tell how big the comet might have been if and when it nearly hit the Earth 1,600 years ago, but if it was massive enough to leave behind large debris that could trigger the kind of airburst that the new study hypothesizes occurred, then it would have at least been big enough to cause major devastation.
The asteroid that hit off the Yucatan Peninsula 66 million years ago and triggered the mass-extinction event that wiped out the non-avian dinosaurs is estimated to have been about six to 10 miles wide, which is a fairly normal size for a comet.
However, that asteroid was also much denser, possibly three to four times thicker than your typical comet, so a six-mile-wide comet would not pack as much of a punch as that asteroid did.
It still would have triggered incredible devastation to the hemisphere it impacted and would likely have triggered a nuclear winter, which would have resulted in the mass extinction of countless species, possibly even humans.
Turns out the bright red Samsung Galaxy S22 Ultra is a big disappointment
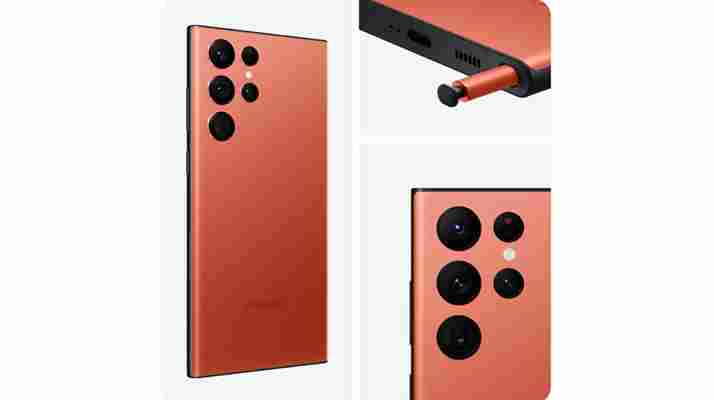
A few days ago I wrote an article about the Samsung Galaxy S22 Ultra , singing the praises of an incredible-looking red version that Samsung had hidden away as an exclusive on its website.
"It's so much better-looking than all the other shades" I wrote in my gushing article on the phone , praising its "warm and energetic feel." I wanted one.
Well, apparently, I was completely wrong. Passionate Samsung fans have reached out to let me know: the bright red Samsung Galaxy S22 Ultra isn't actually that red after all.
Red...ish
After my Galaxy article went live, lots of people who'd bought the red phone wrote in to let me know their feelings on it (if you wrote in, thanks for reaching out - we got so many commenters that we couldn't respond to them all, but we appreciate it!).
Nearly every email we received was from someone who'd bought the device, writing to communicate their disappointment at how the phone looks in real life. Apparently, it's not the same vibrant shade that pictures on Samsung's website show - a descriptive word that cropped up a surprising amount was 'coral'.
Apparently the red Galaxy S22 Ultra looks more coral, or pale-orangey-red, than vibrant fiery red - and that's obviously disappointing for people who wanted an exciting crimson smartphone.
Sure, there's nothing wrong with coral, but if you're buying something that's red, you want it to be... well, red.
The problem with exclusives
The problem with online-exclusive colors is that it's impossible to know exactly how they look - you can't just pop into your local phone store to check out how it looks.
Sometimes companies will try to lure you in to buying from them directly, instead of from carriers or third-party retailers, offering interesting and unique color options that you won't find anywhere else.
Pictures online will only tell you so much, an issue I clearly fell afoul of with my initial coverage. Not only does the hue depend on the screen you're viewing it on, but also, to a smaller amount, on the camera used to capture the press shot in the first place, and any editing done before publishing.
Lots of the time this isn't an issue - if you buy a black phone, you can already predict how it will look. But for brighter colors, like Samsung's red one, even slight changes to the color accuracy of a photo or display can dramatically affect how it looks to people.
Given that the high street has migrated online in recent years, and that lots of retailers, like Samsung, are releasing online-exclusive colors, that means it's very easy for people to buy a phone they think they'll like, only to discover it's not what they expected at all.
So if there's a big enough outcry, perhaps we'll see Samsung shift away from its online-exclusive colors in the future. It doesn't seem likely, since the company has been doing this for a while now, but we can live in hope.